Random Hacking Success — How I Compromised an Admin Panel with Pure Intuition
This wasn’t a bounty program. This wasn’t a targeted red team op. This was one of those unexpected moments where curiosity met persistence — and a bit of stealer intel magic. One of my client sent me a random website asking if I could access its admin panel. The site was a standard LAMP stack setup — Linux, Apache, MySQL, PHP. I said yes. Because PHP + parameters = a playground for exploitation.
Initial Recon
The site (let’s call it target.com) was basic — a blogging platform with:
- Blog listings by category
- Signup/Login/Forgot Password
- Authenticated user features: Commenting, username/email edits
I started with the usual SQLi recon — both GET and POST parameter fuzzing. Spent nearly 2 days testing every form, filter, and input box.
Result?
Absolutely nothing exploitable. Not even a blind Boolean response.
File Upload Attempt
I moved on to the file upload endpoint. I managed to upload a PHP shell, but couldn’t locate its path. Turns out:
- Files were stored with randomized names and UNIX timestamps
- Uploaded files were only visible to admin users
No disclosure, no enumeration success… yet.
Fuzzing Hidden Endpoints
Next, I fired up FFUF with aggressive fuzzing:
- Directory wordlist: directory-list-2.3-medium.txt
- File-specific wordlists: php_files_only.txt / asp_files_only.txt from Karanxa
FFUF Output Snippet:
admin [Status: 301] upload [Status: 301] api [Status: 301] vendor [Status: 301] assets [Status: 301] inc [Status: 301]
Still… nothing juicy.
I even tried SQLi on the /admin/login form — no luck.
Shift in Mindset: Thinking Like a Dev
I was hitting dead ends everywhere. So I switched hats — from hacker to developer. Here’s what changed the game:
On the signup form, the site had a real-time username availability check via API.
That meant I could enumerate valid usernames using this logic:
If a username already exists → API throws "Username already taken"
I brute-tested typical admin usernames:
admin, administrator, admin123, moderator, staff — all unique.
Nothing worked… until I checked the HTML source code.
Breadcrumb in the Source Code
In the HTML head:
<meta name="author" content="XYZCORPORATIONTECH">
Interesting. A web dev company.
I Googled them. Turns out they’re an agency building sites for multiple clients.
I retried enumeration with these usernames:
- xyzcorporation
- xyzcorp
- xyzcorporate
- xyzcorptech
💥 Bingo. xyzcorp was already registered.
Stealer Intelligence for the Win
Time to get creative. I searched leaked stealer logs using their corporate domain to find commonly used passwords.
Found 19 leaked credentials tied to their devs. Most common password?
→ qwer1234 (used in 6 different sites)
I tried:
Username: xyzcorp Password: qwer1234
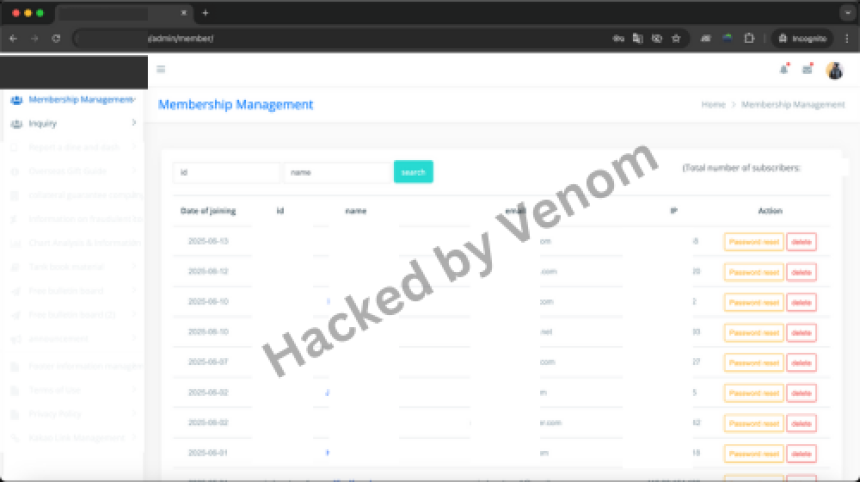
Logged in as admin.
Access to:
- Full user list
- Comment data
- My own previously uploaded PHP shell
Final Outcome
I immediately reported the issue to my client. They patched the vulnerability within hours.
💰 Reward received: $1400 for this intuitive admin takeover.
Lessons & Takeaways
- Enumerating usernames via signup logic is underrated.
- Developers often reuse credentials across client sites.
- HTML meta tags can leak dev/vendor identities
- Stealer logs are a goldmine when you know what to look for.
- Even when all technical vectors fail, human error prevails.